At-hock linking |
This topic contains the following sections:
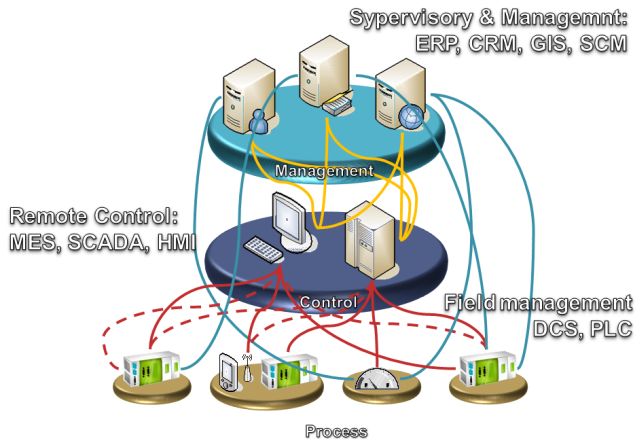
Common integration practice is to achieve short-term ad-hoc objectives by creating dedicated point-to-point links between the subsystems everywhere it is necessary. Most of the links are established between components of the process and control layer, where supervisory control systems receive data from plant-floor devices and subsystems.
If component A needs data from component B, a dedicated link is created. This link provides data from B to A using a proprietary solution acceptable to the component A.
At the next stage of system maturity, new links are created between systems on the business management and control layers. Future enterprise expansion will force to build next direct cross links between business management and production. Additionally, redundant communication links are required to meet an appropriate level of reliability. Finally, we have to deal with communication chaos, which is difficult to be controlled. These chaotic point-to-point links make common resources impossible to be used by many potential client systems.
After years of establishing ad hoc links, the interconnection network becomes very complicated and chaotic causing that we have to deal with the following problems:
Difficult modification and maintenance – each new system will require new links making the structure more and more complex and deepening chaos of communication.
Inefficiency – a lot of the associations are based on a common communication medium, sometimes of a low quality, e.g. enterprise field controller network – the complex structure will necessitate transferring the same data over the network many times and, finally, cause a waste of the bandwidth.
Costs – if communication is based on the third-party toll infrastructure, the fee for the data transfer may be significant. Additionally, a strong dependence on the independent operator increases.
Partial interoperability –the data presentation and description at the link sink is precisely suited to the systems it services and, therefore, data cannot be accessed directly by other systems.
Mess – in a real world enterprise there can be tens, hundreds or even thousands of subsystems in every layer (in the figure above there are only a few components). Maintenance and documentation of such a complex architecture is a real challenge for administrators.
Anarchy – if subsystems have different methods of authorization, authentication and user rights management, it is almost impossible to keep an appropriate level of security. As a consequence, some data can be lost because the rules are too weak or communication cannot be established because the rules are too strong.
The problems presented above grow with the increase of data transfer traffic in an enterprise. On the other hand, production costs optimization demands new subsystems and, as a consequence, their integration with the others. It seems that this contradiction cannot be solved at all without a new systematic design approach methodology and architecture modification. In other words, in any system there is a point (level of complexity) that, having been reached, will even make it impossible to keep the system running. |